Chronicle, Google’s cloud-native security suite, offers advanced solutions like Chronicle SOAR and Chronicle SIEM for automated incident response and real-time security monitoring. Powered by Google Cloud AI, Chronicle accelerates and streamlines security team performance with cost-efficient results.
Key Features:
- Advanced Threat Detection: Uses machine learning and AI to analyze large amounts of data for faster, more accurate threat detection.
- Cloud-Native SIEM: Combines security event management and incident response with deep visibility into cloud workloads and network traffic.
- Security Intelligence Platform: Aggregates logs and security data across your environment to provide a comprehensive threat detection solution.
- Integration with GCP Services: Seamlessly integrates with Google Cloud services for real-time insights into security risks and anomalies.
Read More

Mandiant delivers tailored, industry-specific responses to help organizations proactively protect their critical assets and data. With an extensive suite of cybersecurity services, including incident response, threat intelligence, auditing, and risk management, Mandiant empowers organizations to strengthen their security posture. These services provide sophisticated threat detection, comprehensive analysis, and assessment of external vulnerabilities, equipping businesses with the tools they need to achieve resilient and effective security outcomes.
Key Features:
- Threat Intelligence: Provides real-time threat intelligence to help detect and respond to cyber threats quickly.
- Incident Response and Remediation: Helps organizations investigate and respond to security incidents with expert-led services.
- Cyber Risk Management: Offers strategic insights and recommendations to improve an organization’s security posture.
- Advanced Malware Protection: Identifies sophisticated malware and other threats across environments to enhance overall security.
- Cloud Security Integration: Works across hybrid and multi-cloud environments, offering visibility and control over cloud-based threats.
Read More

BeyondCorp, Google’s Zero Trust framework, delivers secure, VPN-free access with agentless controls, threat protection, and data security for web and SaaS applications. It protects against malware and phishing, while providing Context-Aware Access (CAA), comprehensive reporting, and alerting. BeyondCorp empowers organizations with invisible, secure access from anywhere.
Key Features:
- Zero Trust Security Model: Provides access control based on the identity of users and devices, eliminating reliance on traditional network perimeter defenses.
- Contextual Access Management: Grants access based on factors such as user identity, device health, location, and risk assessment.
- End-to-End Encryption: Ensures data is encrypted both in transit and at rest, offering an extra layer of security for sensitive information.
- Device and User Authentication: Employs multiple authentication methods like multi-factor authentication (MFA) and device trust to ensure only authorized users and devices can access corporate resources.
- Seamless Integration with Google Cloud: Provides easy implementation within Google Cloud environments, leveraging existing security infrastructure.
Read More

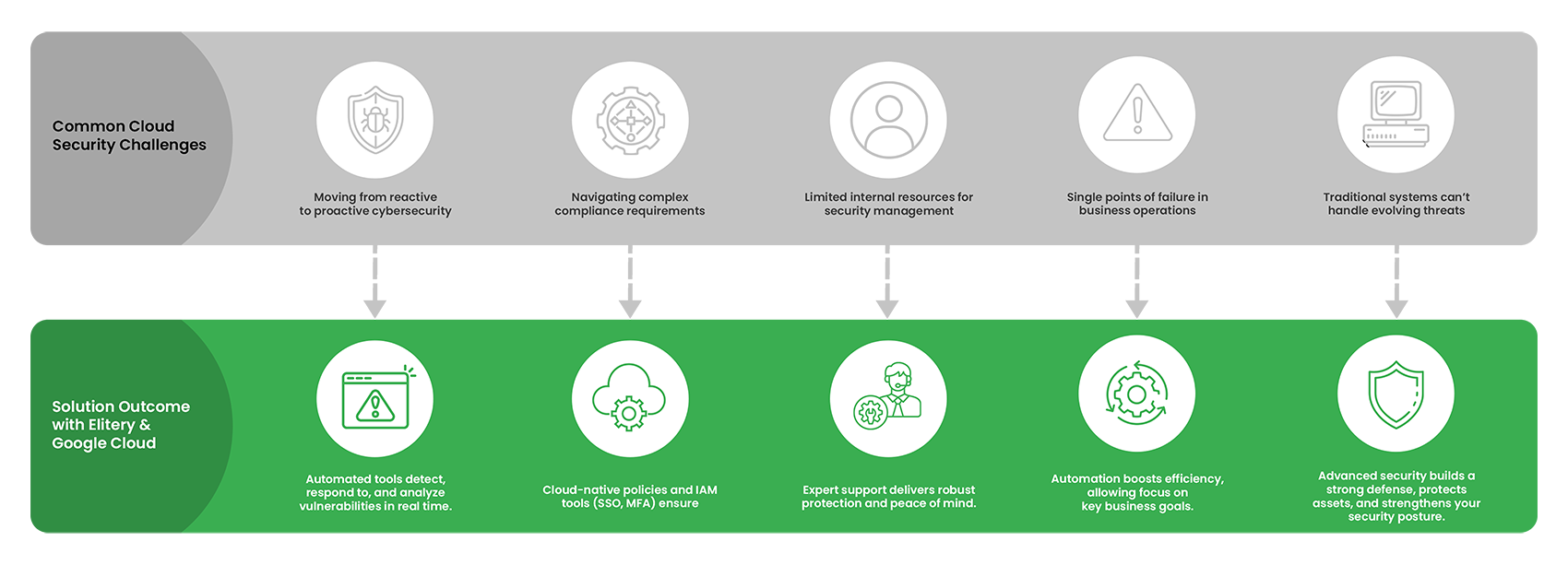
Google Cloud’s Security Command Center provides centralized visibility and control over your cloud infrastructure, enabling you to identify and mitigate vulnerabilities and threats in real time. With advanced posture management, threat detection, and built-in remediation, it ensures proactive and reactive security for your organization’s data, code, and identities. Powered by Google’s cutting-edge technology and a planet-scale data lake, it streamlines security response and supports compliance reporting, making it an essential tool for comprehensive cloud security management.
Key Features:
- Centralized Security Monitoring: Offers a single-pane-of-glass view for managing your Google Cloud security and compliance posture.
- Automated Risk Discovery: Automatically detects vulnerabilities and misconfigurations in cloud resources across Google Cloud services.
- Security Insights and Recommendations: Provides actionable recommendations based on real-time security data to reduce risk and improve configurations.
- Threat Intelligence Integration: Incorporates external threat intelligence sources to enhance risk detection and security response.
- Cloud Asset Inventory: A detailed inventory of cloud resources and configurations to help manage security and compliance.
Read More

VirusTotal is a powerful solution that scans files, URLs, and domains using multiple antivirus engines to determine their safety. By providing detailed context and analysis, it helps users identify whether a file or site is malicious or secure. VirusTotal enhances cybersecurity by offering a comprehensive, multi-layered approach to threat detection and prevention.
Key Features:
- Malware Detection: Scans files, URLs, and domains to detect potential threats using a variety of antivirus engines.
- Threat Intelligence Sharing: Shares threat data across organizations to strengthen collective cybersecurity efforts.
- File and URL Analysis: Provides detailed reports on suspicious files and URLs, helping organizations identify malicious behavior.
- Real-Time Data Feeds: Continuously provides updated data to help identify emerging threats and vulnerabilities.
- API Integration: Allows integration with other security tools and workflows to streamline threat detection.
Read More

reCAPTCHA protects your website from fraud and abuse while ensuring a seamless experience for legitimate users. By using advanced risk analysis and adaptive challenges, it prevents bot attacks and malicious activities. It also defends against common web threats like credential stuffing, account takeovers, and scraping, allowing only valid users to access your site.
Key Features:
- Bot Protection: Prevents automated software (bots) from abusing online services by distinguishing between human and non-human interactions.
- User-Friendly Verification: Provides a frictionless user experience with simple “I am not a robot” challenges or invisible CAPTCHA for users.
- Advanced Risk Analysis: Uses machine learning to evaluate user interactions, providing real-time risk scores to block suspicious activities.
- Adaptive Challenges: Dynamically adjusts CAPTCHA challenges based on the perceived risk of the request.
- Fraud Prevention: Protects websites from fraud, abuse, and account takeovers by ensuring that only legitimate users can access services.
Read More